1. General Overview
1.1. What is a Public Key?
A Public Key is a special sequence of numbers or letters that you can think of as an “address” for your cryptocurrency.
Public Key is often used as a wallet address, to encrypt data for sending, and to verify digital signatures.
1.2. What is a Private Key?
A Private Key is a special string of characters, similar to a private password, used in the cryptocurrency market to sign transactions and authenticate access to your account, thus protecting and controlling your digital assets.

For example, when you create a Metamask wallet account, you will receive a Public Key (wallet address) and a Private Key (private key).
- Public Key (Wallet Address): 0x89384Dn738Bcd892…
- Private Key: 968932F8H79CE…
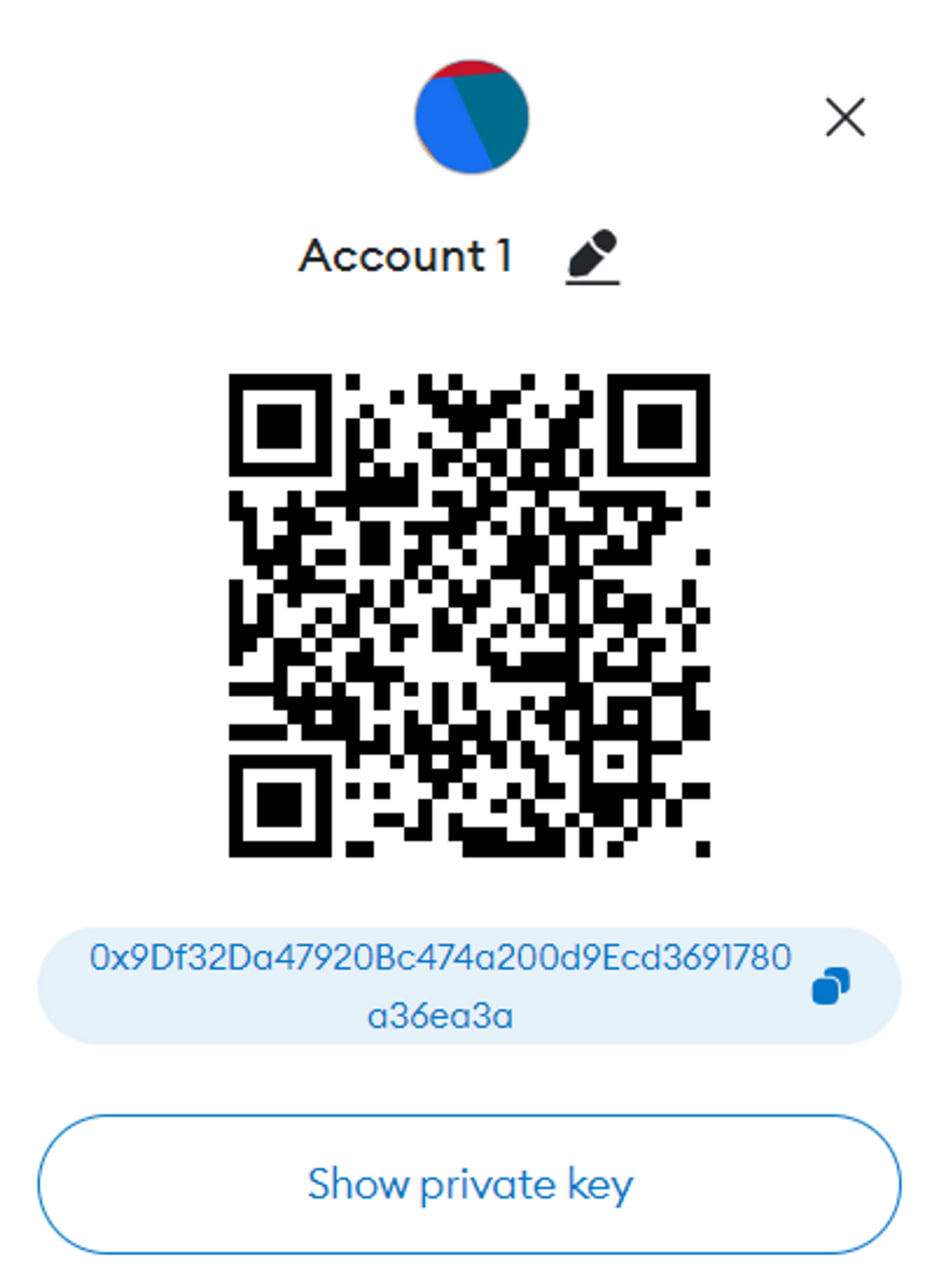
2. Origin
The concept of Public Key and Private Key originates from the field of cryptography, which is an essential area in computer science and information security.
This principle was developed in the 1970s by various researchers, but one of the key foundations for developing public key and private key systems is the RSA (Rivest-Shamir-Adleman) public key encryption algorithm, which was published in 1977 by Ron Rivest, Adi Shamir, and Leonard Adleman.
The RSA algorithm is a crucial part of Public Key Cryptography (PKC), allowing users to create a pair of keys consisting of a public key and a private key.
The public key can be shared openly and is used to encrypt data, while the private key is known only to the owner and is used to decrypt data that has been encrypted with the corresponding public key.
3. How Does a Public Key Work?
A Public Key can be used in two main scenarios: to identify and to secure information.
Sender and Receiver: Imagine you are the sender of information and you know the recipient's Public Key—this is their wallet address.
Encryption Step: To begin, you use the recipient's Public Key to encrypt your information. This is like putting a letter in a secure locked box that only the recipient can open.
Sending Information: Now, you send the encrypted information to the recipient. Anyone can see the information, but only the recipient has the correct key to unlock the box.
Recipient Decrypts: When the recipient receives the information, they use their Private Key to decrypt it. This Private Key belongs only to them, like a private key to open the box.
In summary, the Public Key is used to encrypt information before sending, and the recipient uses the Private Key to decrypt it.
In a blockchain context, when a user wants to receive funds from another person, they need to provide their wallet address.
For example, if a user is using a Metamask wallet to transact, they will provide their Public Key (wallet address) to the sender to receive 100 USDT. Once the sender has sent 100 USDT to the user's wallet address, the user will use their Private Key to log into the wallet and access the 100 USDT.
Note: Users can freely share their Public Key, but they must keep their Private Key secure and not share it with anyone. If someone obtains your Private Key, they will gain access to your assets and can deplete your account!
4. How to Differentiate Between Public Key and Private Key
Public Key and Private Key are two components of the key pair in a public key cryptography system. Below is a table distinguishing Public Key from Private Key:
| Public Key | Private Key | |
|---|---|---|
| Purpose | Serves as a wallet address to receive cryptocurrency. | Used to sign transactions and authenticate access to the account. |
| Publicity | Can be shared with anyone | Should not be shared with anyone |
| Key Recovery | Can recover the public key from the private key | Cannot be recovered if the private key is lost |
| Risk When Exposed | None | Affects asset security |
| Shortened Version | Yes (Address) | No |
5. Conclusion
Public Key and Private Key are two commonly used terms in the crypto world. Proper storage and protection of these keys are essential to avoid losing your account. Always keep your passwords and Private Keys confidential to prevent unauthorized access to your account or information.
Read more:

 English
English Tiếng Việt
Tiếng Việt


.jpg)

.jpg)










