
1. What Is a Permissionless Blockchain?
A permissionless blockchain, often called a public or trustless blockchain, is an open network that allows anyone to join, read the ledger, and participate in the consensus mechanism. No prior approval or identity verification is required. Participants are pseudonymous or anonymous, and the network relies on decentralized governance mechanisms, typically powered by cryptographic tokens.
Key Characteristics:
-
Openness and Accessibility: Anyone can join the network, validate transactions, and read the ledger.
-
Transparency: All transaction data is publicly available and verifiable by any participant.
-
Decentralization: No central authority or gatekeeper controls the network.
-
Anonymity: Users are often represented by cryptographic addresses, not real-world identities.
-
Incentive-driven Participation: Tokens and other digital assets are used to encourage network maintenance and honest behavior.
-
Open Source Development: Most permissionless blockchains rely on communities of developers contributing to the protocol’s evolution.
Examples: Bitcoin, Ethereum, Solana, and other Layer 1 public blockchains are well-known examples of permissionless architectures.
2. What Is a Permissioned Blockchain?
A permissioned blockchain — also referred to as a private blockchain or enterprise blockchain — restricts access to specific, known participants who must be authorized before interacting with the ledger or participating in consensus. These networks are often used by companies, industry alliances, or government agencies that require strong governance and data control.
Key Characteristics:
-
Restricted Access: Only approved participants can view or write data to the ledger.
-
Partial Decentralization: Governance is distributed among a group of trusted parties, but not as broadly as in permissionless systems.
-
Identity Verification: All nodes are known entities, typically assigned specific roles and permissions.
-
Custom Governance: The rules of consensus and validation are controlled by the organization(s) operating the network.
-
Private Development: Development is usually carried out by a core internal team or consortium members.
-
Configurable Transparency: Data visibility and auditability can be fine-tuned to suit the needs of the network operators.
Examples: Hyperledger Fabric, R3 Corda, Quorum, and other blockchain platforms designed for enterprise use cases fall into the permissioned category.
3. Comparing the Two Models: Pros and Cons
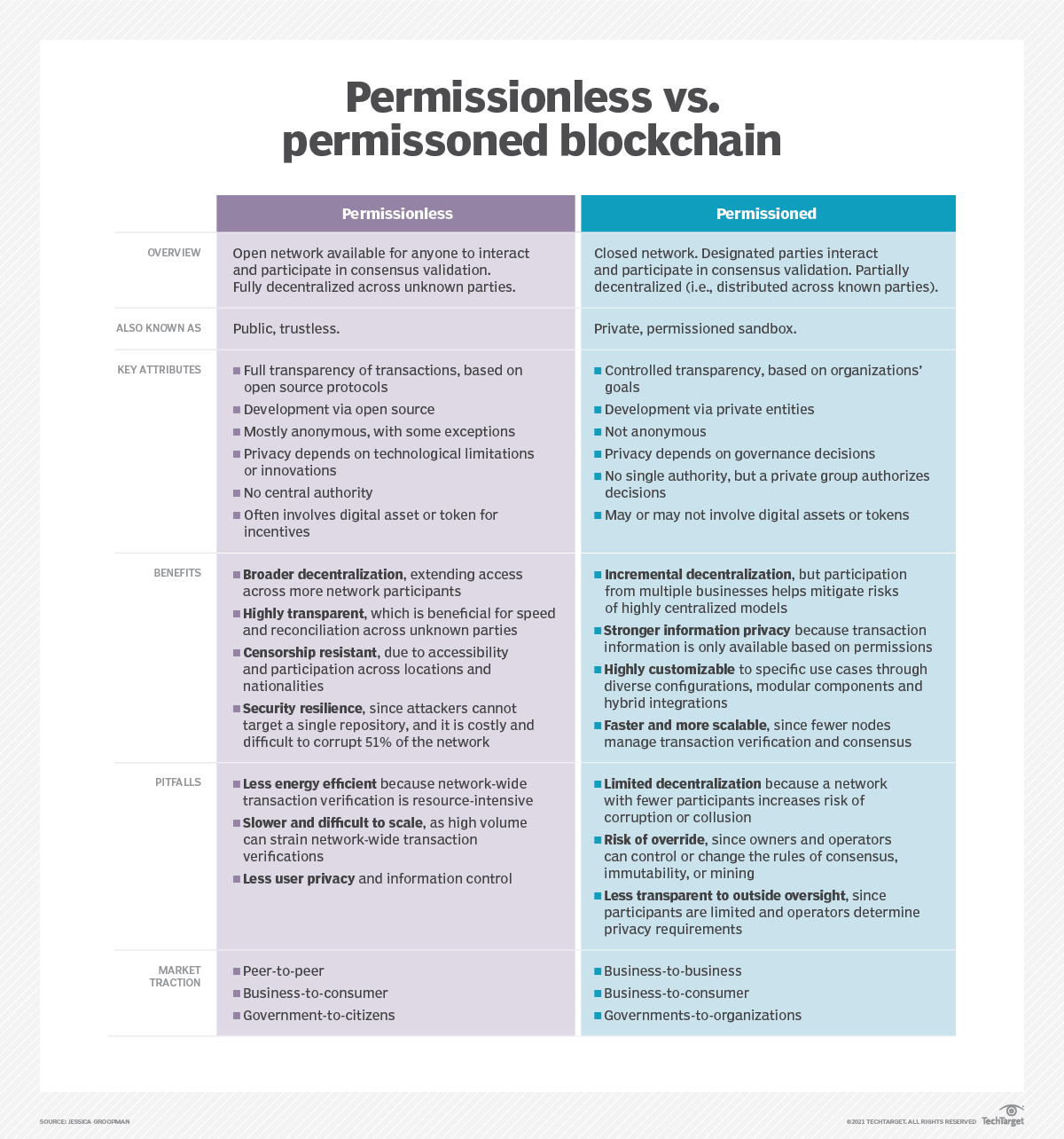
3.1. Permissionless Blockchain
Pros:
-
High decentralization: No single entity can dominate or censor the network.
-
Transparency: All transactions are publicly visible and verifiable.
-
Security: Distributed architecture and cryptographic consensus mechanisms reduce the risk of centralized failure or manipulation.
-
Censorship resistance: Especially useful in politically or economically unstable environments.
Cons:
-
Scalability challenges: Network-wide validation processes slow transaction speeds and limit throughput.
-
Energy inefficiency: Especially in proof-of-work systems, massive computational resources are required.
-
Limited privacy: Public transparency comes at the cost of data confidentiality.
-
Complex regulatory compliance: Anonymity and decentralization may conflict with legal and regulatory frameworks.
3.2. Permissioned Blockchain:
Pros:
-
Greater performance and scalability: Fewer nodes and streamlined consensus protocols result in faster transaction processing.
-
Privacy and confidentiality: Data is visible only to authorized participants.
-
Customizability: Protocols, rules, and interfaces can be tailored for specific use cases.
-
Incremental decentralization: Offers a path toward collaboration without the risks of fully open systems.
Cons:
-
Risk of collusion: Smaller groups of validators may be vulnerable to corruption or unilateral decision-making.
-
Weaker transparency: Less visibility can hinder trust, especially for public-facing systems.
-
Governance control: System rules can be changed more easily, raising concerns about immutability.
-
Lower community engagement: Lack of tokens or incentives may reduce participation and innovation.
4. Hybrid Approaches: The Best of Both Worlds
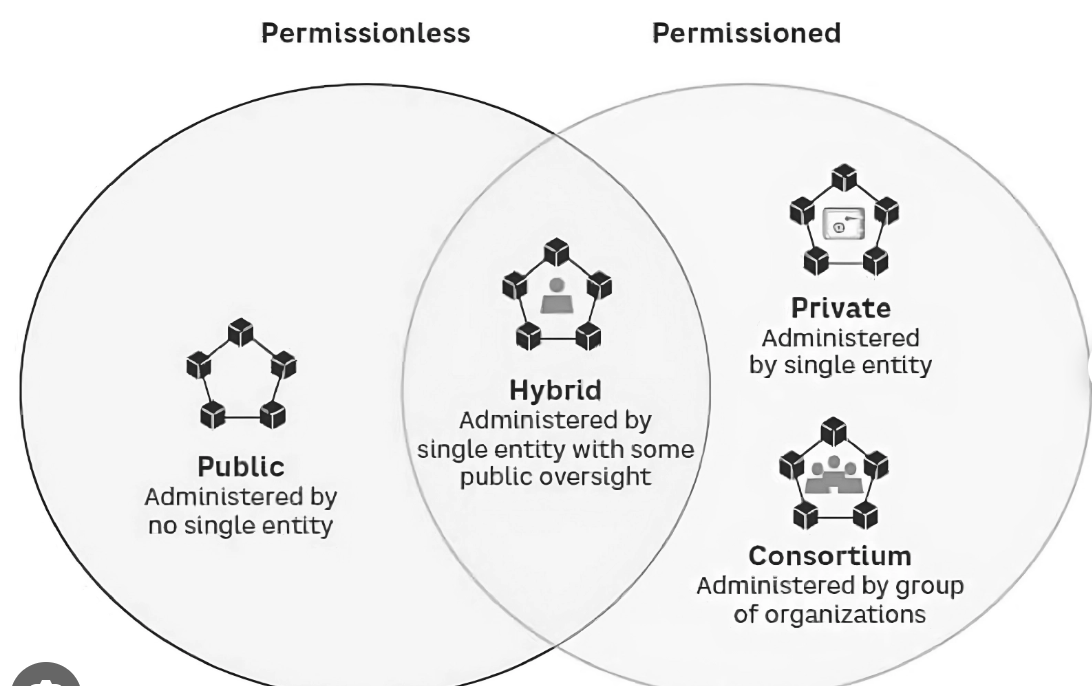
In practice, many real-world systems will blend elements of both permissioned and permissionless models. These hybrid blockchains offer a flexible architecture where certain parts of the network are open and public, while others remain private and controlled.
For example, a public blockchain may be used for timestamping and proof of existence, while sensitive transactional data remains on a private ledger. This approach provides interoperability, efficiency, and selective transparency, making it ideal for complex ecosystems that span industries, borders, and regulatory frameworks.
5. Use Case Comparison: Choosing the Right Blockchain Model
5.1. Permissionless Blockchain Use Cases
-
Cryptocurrency and DeFi applications
-
Crowdsourced fundraising (ICOs, IDOs)
-
Decentralized storage platforms (e.g., IPFS, Filecoin)
-
Open gaming ecosystems and NFTs
-
Cross-border remittances and open financial services
5.2. Permissioned Blockchain Use Cases
-
Supply chain tracking and provenance (e.g., food, pharmaceuticals)
-
Healthcare data sharing among clinics and research institutions
-
Digital identity and credential verification
-
Insurance claims and automated settlement
-
Trade finance and consortium-based banking
6. Conclusion
Permissioned and permissionless blockchains represent two ends of a broad architectural spectrum. Both offer unique advantages — and neither is inherently superior. The key to long-term success is choosing or designing an infrastructure that fits your use case, regulatory environment, and ecosystem dynamics.
Blockchain is not a magic solution to all digital problems, but a modular set of tools and principles. When applied thoughtfully, it can help build more transparent, efficient, and collaborative systems. Businesses must resist the hype, look beyond technological buzzwords, and design blockchain systems with clarity, purpose, and flexibility in mind.
Read more:

 English
English Tiếng Việt
Tiếng Việt






.jpg)





