1. What Is a Hash and How Does It Work?
A hash is the output of a cryptographic algorithm that transforms any input—whether it’s a sentence, a transaction, or an entire document—into a fixed-length string of characters. Regardless of how large or small the input is, the result is always of consistent length. In Bitcoin, for example, the SHA-256 hash function produces a 64-character hexadecimal string.
What’s striking about hashes is that even the slightest change in the input completely alters the output. A single character difference, such as changing “blockchain” to “Blockchain,” generates an entirely different hash. This phenomenon, known as the avalanche effect, makes it practically impossible to predict or reverse-engineer the original input from its hash. In other words, hashing acts like a one-way street—easy to compute, but extremely difficult to decode.
2. The Role of Hashing in Blockchain Architecture
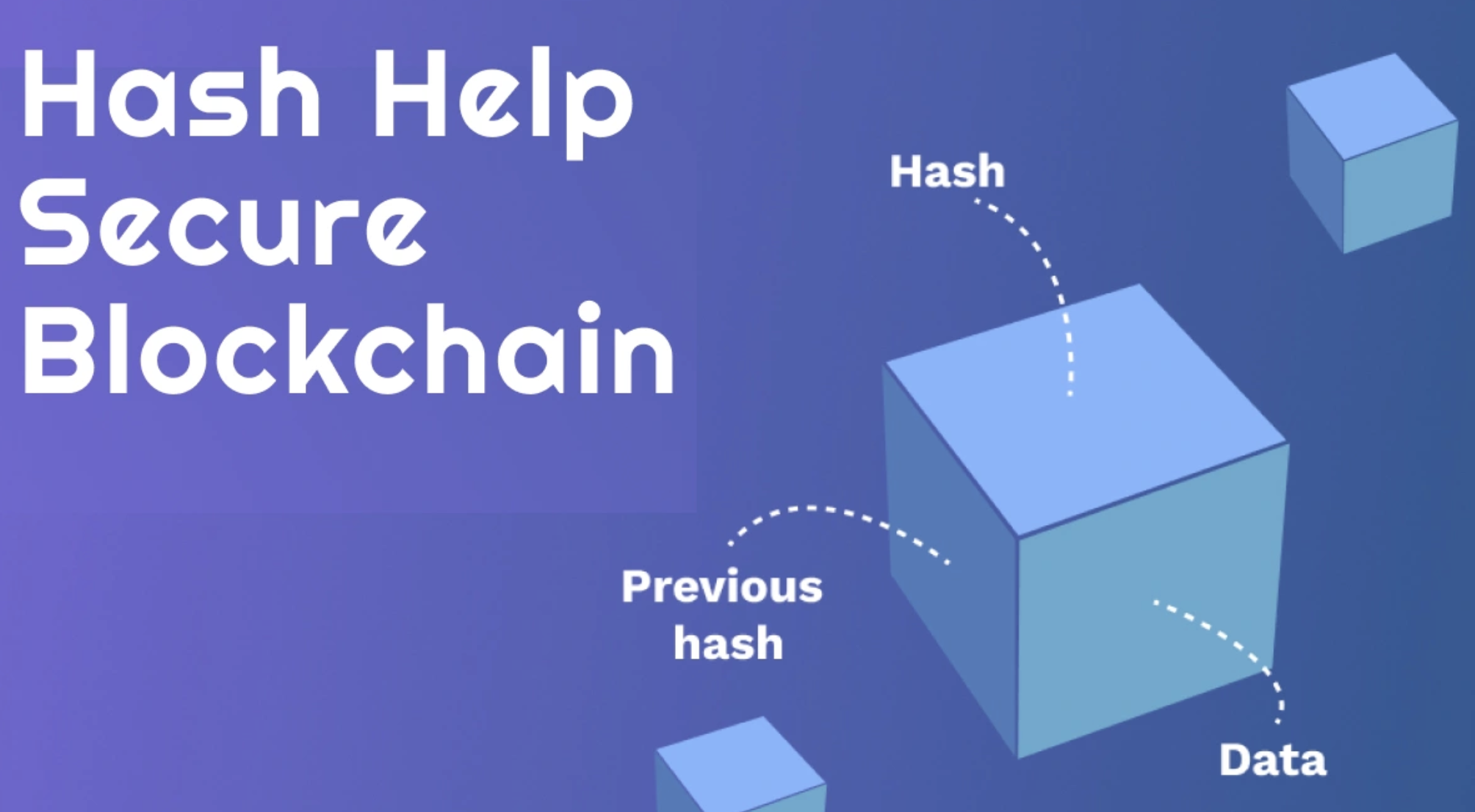
To grasp why hashing is indispensable, it’s important to understand how blockchain works. Each block in a blockchain contains:
-
A list of validated transactions
-
A timestamp
-
A unique hash of the current block
-
The hash of the previous block
-
A nonce, used in mining under Proof-of-Work systems
This design creates a chain-like structure where every block is cryptographically linked to the one before it. If someone attempts to alter a block, the change would modify that block’s hash—immediately breaking the link to the next block. Such a disruption is easy to detect, exposing tampering attempts at once.
This mechanism ensures that once a transaction is recorded on the blockchain, it becomes extremely difficult to alter, earning blockchain the status of being “immutable.”
2.1. Security Through Tamper Resistance
Hashing is a silent guardian of blockchain integrity. Because each block contains the hash of the previous block, tampering with any block would require recalculating not just that block’s hash, but also the hashes of every subsequent block.
In large networks like Bitcoin, this is virtually impossible due to the sheer computational power required. An attacker would have to re-mine hundreds or thousands of blocks faster than the rest of the network—a feat that would demand control of more than 50% of the total computing power. Such an attack, known as a “51% attack,” is theoretically possible but prohibitively expensive and has never been successfully executed on Bitcoin.
This built-in resistance to tampering makes blockchain particularly valuable for sectors that rely on data integrity, such as finance, healthcare, and legal record-keeping.
2.2. Proof of Work: Making Hashes Work Hard
Hashing also plays a central role in the Proof of Work (PoW) consensus mechanism. Before a new block can be added to the blockchain, miners must solve a complex mathematical puzzle. The challenge is to find a nonce (a random number) that, when hashed with the block’s contents, produces a hash that begins with a certain number of zeros.
This process is purely trial and error. It may take millions or billions of attempts before the correct hash is found. The difficulty of the task acts as a gatekeeper, slowing down block creation and making it costly to interfere with the system.
In the case of Bitcoin, this puzzle-solving process ensures that blocks are mined approximately every 10 minutes. It also gives the network a built-in level of security, since altering a block would require redoing all the computational work—again, an almost impossible task for attackers.
2.3. Ensuring Data Integrity with Merkle Trees
Within each block, hashing is also used to verify the validity of individual transactions. Blockchain systems employ a structure called a Merkle tree, where every transaction is hashed and combined in pairs. These pairwise hashes are themselves hashed, forming a tree that eventually culminates in a single Merkle root.
This structure allows users and nodes to verify whether a specific transaction is part of a block without needing to download the entire block. It ensures efficiency while maintaining data integrity, a critical feature for devices with limited storage or bandwidth.
This approach is especially important for light clients in mobile and IoT applications, where verifying transactions without full node participation increases speed and accessibility.
3. Hashing in Real-World Blockchain Events
The practical importance of hashing has become evident in several high-profile blockchain incidents. For instance, during the DAO hack on Ethereum in 2016, the immutability of the blockchain—secured by hashing—presented a moral and technical dilemma. While funds were stolen due to a smart contract vulnerability, the integrity of the transaction history could not be altered without fundamentally changing the blockchain. This led to a controversial hard fork, splitting the Ethereum community into Ethereum (ETH) and Ethereum Classic (ETC).
Though not a direct flaw in hashing, the incident highlighted the unforgiving nature of immutable data, which hashing makes possible. It also demonstrated that blockchain’s strength—security and trustlessness—can lead to difficult decisions when human error is involved.
4. Conclusion
While often overshadowed by flashier components like smart contracts and cryptocurrencies, hashing remains the silent engine behind blockchain’s promise of trust and security. It links blocks together in a tamper-proof chain, enforces transparency, deters malicious activity through computational cost, and enables fast, verifiable transactions at scale.
Hashing alone does not make blockchain perfect. It does not protect against poorly written code, insider manipulation, or flawed governance. However, without hashing, blockchain would collapse under the weight of its own promises.
In a world increasingly dependent on digital records, hashes serve as digital fingerprints—silent, mathematical proofs that the truth has not been altered. As blockchain technology continues to evolve into sectors such as central bank digital currencies (CBDCs), carbon tracking, and decentralized identity, the humble hash will remain its most dependable line of defense.
Read more:

 English
English Tiếng Việt
Tiếng Việt







.jpg)





