1. What is crypto dust?

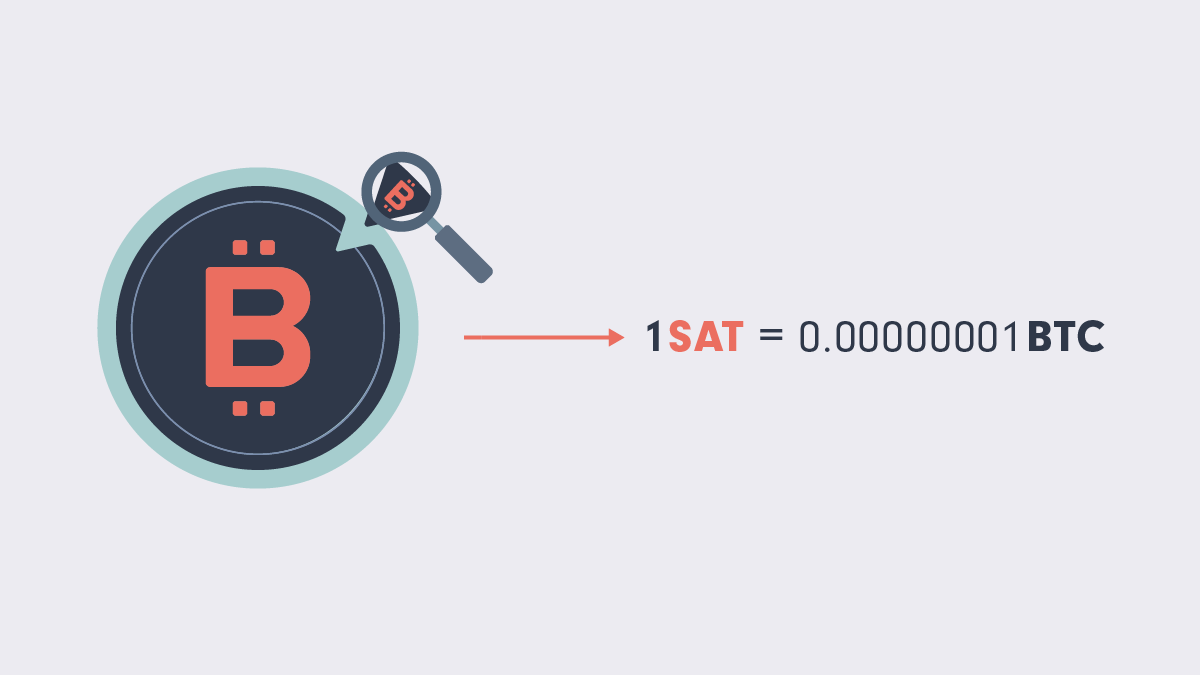
Crypto dust refers to tiny amounts of cryptocurrency sent to various wallet addresses, often unintentionally or as a result of rounding errors from transactions. These small amounts can be so minuscule that they are considered insufficient to be used in a typical transaction. For example, Bitcoin's "dust limit" is around 546 satoshis, which is worth a fraction of a cent.
While dusting in itself is not inherently malicious, it can accumulate over time or be used in specific legitimate scenarios. For instance, cryptocurrency exchanges may offer users the ability to convert dust into other tokens, or marketing campaigns may use dusting as a way to reach out to wallet holders with promotional messages. However, dust can also serve as a tool for malicious actors with harmful intentions.
2. What is a crypto dusting attack?
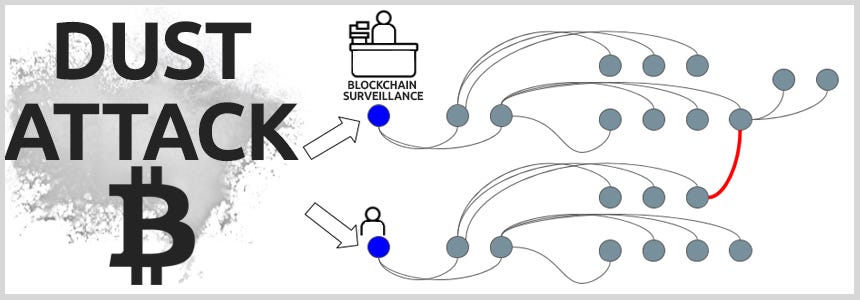
A crypto dusting attack occurs when an attacker sends small amounts of cryptocurrency (dust) to multiple wallet addresses in an attempt to track down the identities of the wallet holders. While the dust itself is not enough to steal funds, it allows attackers to trace transactions and gather information about the target’s activities.
The key to a dusting attack is the transparency of blockchain networks. Despite being pseudonymous, blockchain transactions are traceable, meaning every transaction is publicly visible. By analyzing a series of transactions involving the dust, an attacker can link various wallet addresses together and potentially identify the individuals behind them. The goal is not to steal crypto directly but to deanonymize the wallet holders for purposes such as identity theft, phishing scams, blackmail, or cyber-extortion.
3. Are all dusting attacks scams?
While many dusting attacks are malicious, not all instances of receiving dust are scams. There are legitimate uses of dusting that are not aimed at compromising privacy. For example, some governments may use dusting techniques to trace illegal activities, such as money laundering or tax evasion. Developers may also use dusting as part of stress tests for blockchain systems, ensuring that the network can handle transactions under extreme conditions.
Furthermore, crypto traders might receive dust during routine trades, which can be converted into native tokens without posing any security risks. In these cases, dusting is not part of a scam or attack, but simply an incidental byproduct of blockchain transactions.
4. How does a dusting attack work?

The process of a dusting attack begins when a malicious actor sends tiny amounts of cryptocurrency to a large number of wallet addresses. Most users won’t even notice the small amounts, as they are typically too small to spend or trade.
The attack is effective when the victim unknowingly spends or transfers these tiny amounts of dust along with larger sums in a future transaction. This action creates a connection between the dust and the rest of the wallet's funds. By analyzing these transactions, an attacker can link the dust to the user’s identity, especially if the funds are subsequently moved to a centralized exchange that requires Know Your Customer (KYC) information. Once the attacker identifies the individual behind the wallet, they can use this information for malicious purposes, such as phishing or extortion.
5. Can dusting attacks steal crypto?
.jpg)
In a traditional dusting attack, the goal is not to steal cryptocurrency directly but to de-anonymize wallet owners. The small amounts of dust sent to wallets cannot be used to access or steal crypto, but they enable attackers to track a user’s activities and associate their wallets with personal data.
However, the sophistication of dusting attacks has increased in recent years. In addition to tracking wallet activities, attackers have begun using more advanced techniques. For instance, they may disguise malicious tokens as legitimate airdrops or free giveaways, leading victims to phishing sites where they can be tricked into revealing sensitive information or connecting their wallets to malicious smart contracts. This opens the door for attackers to steal crypto assets, including NFTs and other tokens.
6. Ways to identify crypto dusting attacks
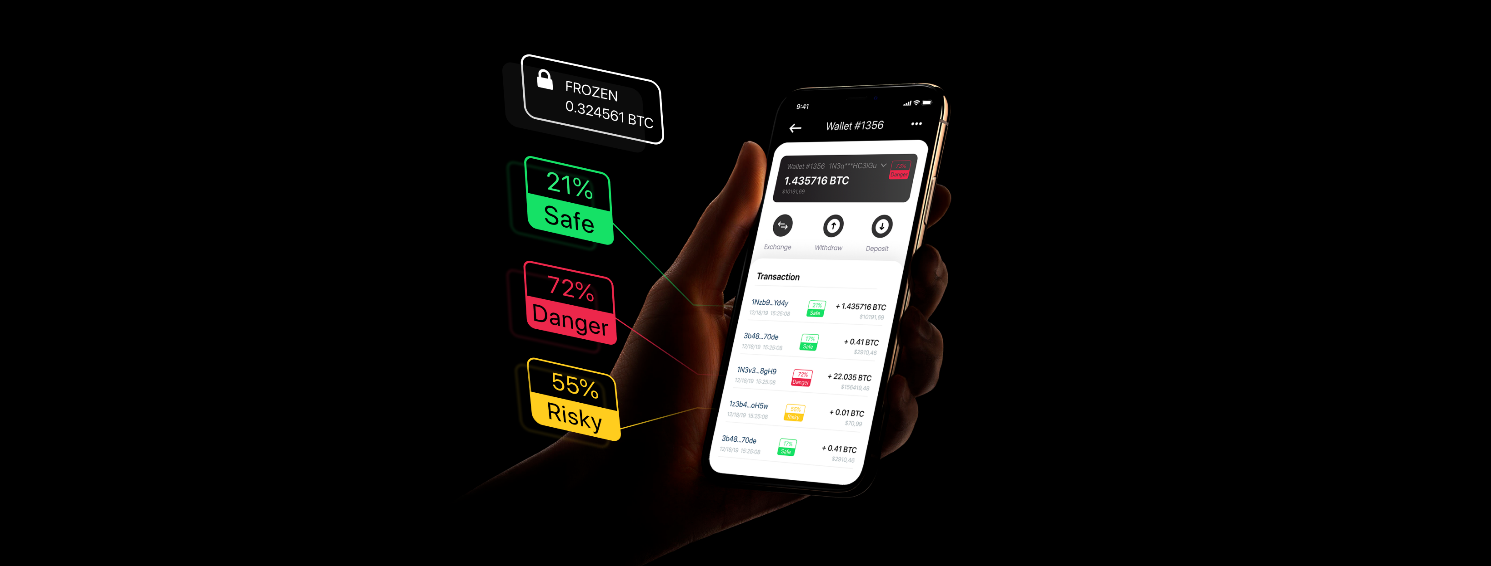
A crypto dusting attack is often evident when users notice small amounts of cryptocurrency in their wallets that they did not initiate or expect. These tiny amounts are usually not sufficient for a transaction but are visible in the wallet’s transaction history.
To confirm whether an attack has occurred, users should examine their wallet history for suspicious dust deposits. Furthermore, since centralized exchanges are required to comply with KYC regulations, the data of users who interact with the dust may be stored, making them more vulnerable to subsequent phishing attempts or hacks.
7. Ways to prevent dusting attacks

Although crypto dusting attacks may seem like an unlikely threat, there are several measures that users can take to protect themselves:
-
Do not move dust: One of the simplest ways to avoid falling victim to a dusting attack is not to use the dust received in your wallet. Since dusting relies on linking multiple addresses, not moving the dust prevents attackers from tracing it.
-
Use privacy tools: Leverage privacy-enhancing technologies such as Virtual Private Networks (VPNs) or The Onion Router (TOR) to enhance your anonymity online. These tools make it harder for attackers to trace your transactions or monitor your activities.
-
Use a hierarchical deterministic (HD) wallet: HD wallets generate new addresses for each transaction, which can make it difficult for attackers to link multiple addresses to a single wallet.
-
Convert dust: Many exchanges and wallet providers offer services that automatically convert dust into usable tokens, thus eliminating the possibility of tracking the dust and reducing privacy risks.
-
Stay vigilant: Regularly check your wallet’s transaction history for signs of dust and be cautious when interacting with new tokens or clicking on links from unknown sources.
Conclusion
Crypto dusting attacks are a growing concern in the cryptocurrency world. While they do not directly steal funds, they can compromise your privacy and expose you to a range of malicious activities. Understanding how dusting attacks work and taking steps to protect yourself—such as using privacy tools, avoiding dust transactions, and keeping a close eye on your wallet—can help minimize the risks associated with these types of attacks. As blockchain technology continues to evolve, so too will the sophistication of cyber threats, making it essential for cryptocurrency users to stay informed and vigilant.

 English
English Tiếng Việt
Tiếng Việt.png)
.jpg)

.jpg)
.jpg)
.jpg)

.jpg)
.jpg)

.jpg)
.jpg)
.jpg)




